Background – Purpose of the Project
In March 2008 the Digital Security research group of the Radboud University Nijmegen made public that they performed a complete reverse-engineering and were able to clone and manipulate the contents of an OV-Chipkaart which is using MIFARE Classic chip (see link).
For demonstration they used the Proxmark3 device, a 125 kHz / 13.56 MHz research instrument.

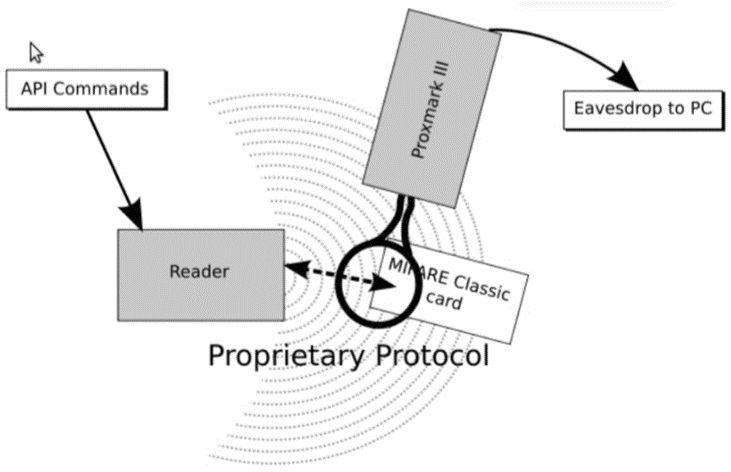
Additionally, there are a number of attacks that work directly on a card and without the help of a valid reader device. More information about card-only attack can be found here:
In short, the MIFARE Classic card memory content, even protected with secret keys A or B, can be easily read using hardware like the Proxmark3 or with a cheap RFID reader/writer and the MFOC software tool. Non Unique ID changeable MIFARE cards are also easy to buy and relatively cheap (under $2). Using these cards an attacker is able to create a perfect clone of any MIFARE Classic card (including UID).
Case study – water filling station
Click the link -> Plan To Develop 26 Water Filling Stations In Three Regions

One of our customers from the Middle East had a problem with such cloned MIFARE cards. Their product is water filling stations located in hard-to-reach places in the desert – without Wi-Fi coverage. Users have RFID cards with the number of gallons of water they have purchased being stored in the card’s memory. After inserting the card into the reader located in the machine, the user indicates the required amount of water and starts the pump system. After filling the containers, the amount of credit on the card is reduced by the amount of water taken. The solution was simple and effective until someone started cloning cards. The client was suffering heavy losses due to cloned cards enabling stolen water.

Challenges to Address
The customer was constrained that any solution to replace the existing RFID reader/writer needed to be completely swap out/ reverse compatible to the old reader as far as the host system was concerned. This meant that anti-cloning measures had to be implemented without replacing or modifying the expensive and extensive water dispenser equipment, including the host control hardware and software. Our first proposal was to replace all user cards with MIFARE Plus/MIFARE DESFire cards, which are better secured. Unfortunately, this would cause problems because several thousand users would have to replace their cards and the transition period would last many months.
Technology Developed
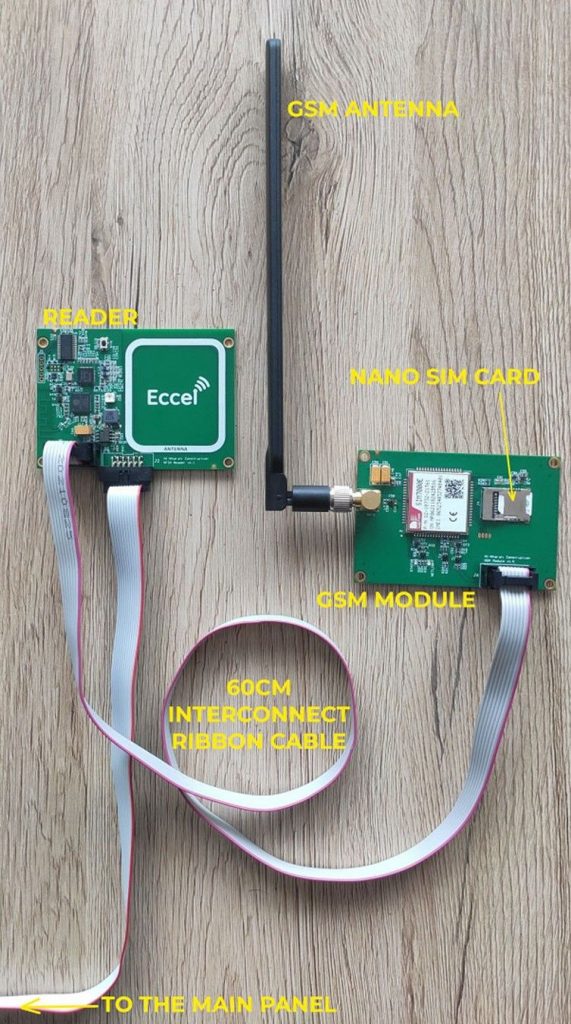
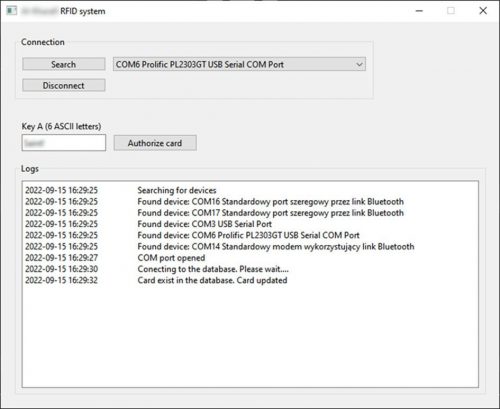
Eccel proposed and developed another solution that addressed the problem of cloning without any host system hardware or software modifications. This solution was to develop a new RFID reader with a GSM module that then connected to a cloud database containing all genuine card details and the number of credits assigned to them. The customer previously used our old OEM MICODE RS232 reader, so the new device had to be compatible with the previous reader.

Eccel designed a new version of the reader and the GSM module based on the SIM7000G chip which is able to connect to a cloud database to verify the cards. Eccel developed a mySQL database and we host this in the cloud for the customer.
The Final Product – RFID Reader with Cloud Based Verification
This is contained within the water delivery control panel invisible to the user.
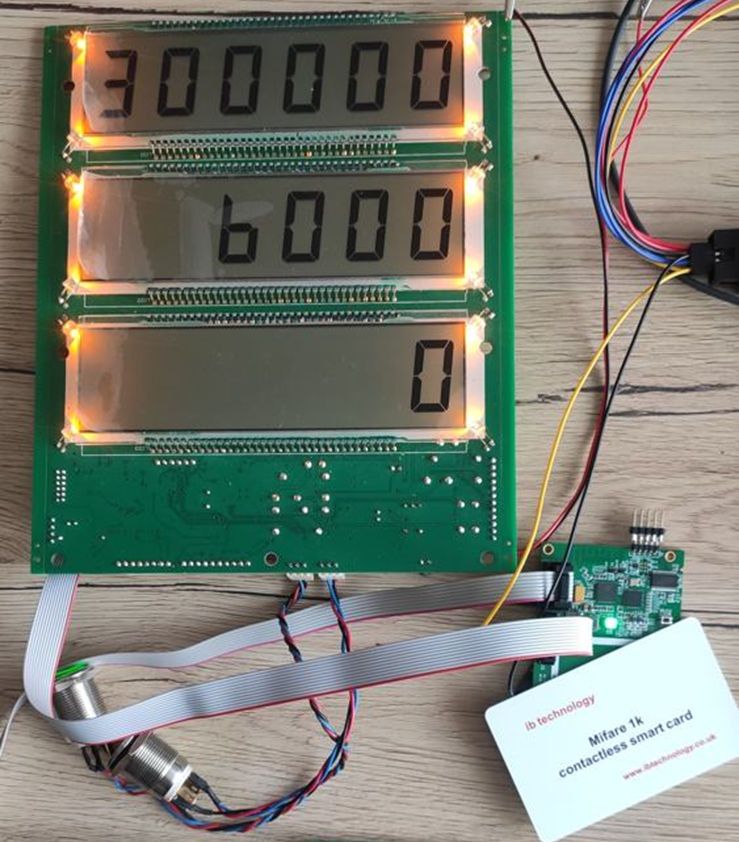
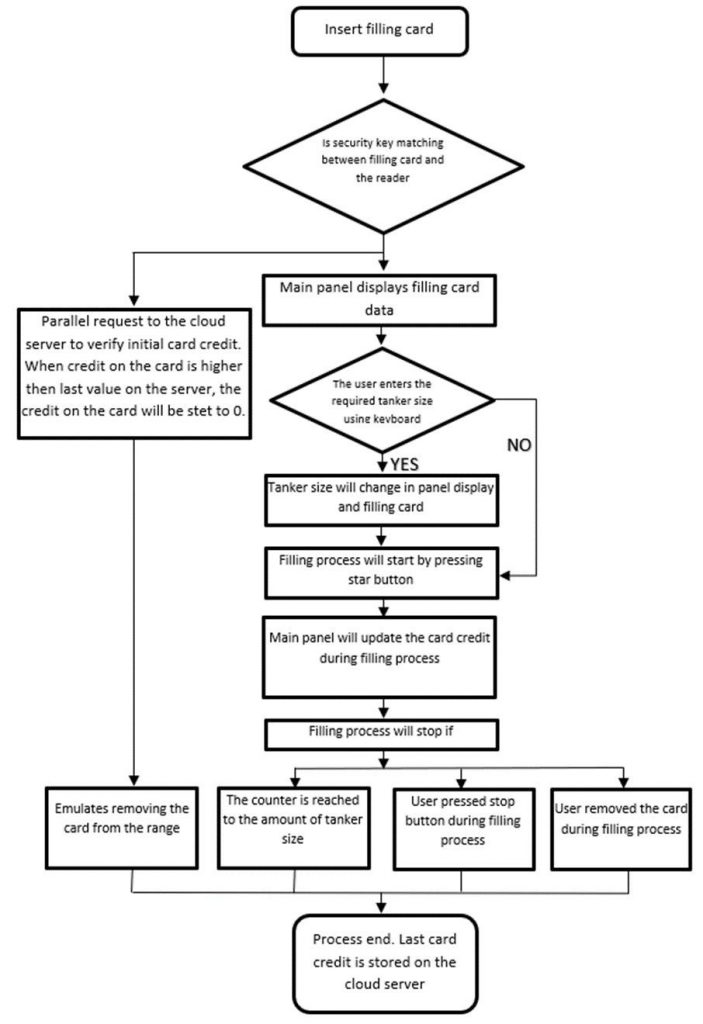
Once the user inserts a card into the water filling station slot provided, the reader reads the amount of credit stored on the card. Then, the GSM module connects to the cloud database and looks for the given card UID in the database. It will then compare the number of credits stored in the card and the number of credits saved in the database. If both numbers are the same the reader will accept the card and allow the user to fill their container. After the filling procedure the reader will decrease the number of credits on the card as well as in the database.
If someone clones the card, there will be two identical cards in the system with the same number of credits. The reader will accept one of them (even the cloned one), but if then, another person will try to use the second card the number of credits won’t match, and the reader will block both cards – they will be just removed from the database and blacklisted. Whenever someone tries to use this card, system administrators will be notified, and the hacker can be easily traced.
In parallel with the readers installed in water filling stations, Eccel also designed several authorization readers in 3D plastic housings and a PC application enabling the customer to add new cards to the database.

This project – RFID Reader with Cloud Based Verification – demonstrates how Eccel can prevent card cloning theft by using 2-stage verification checking of RFID card contents against a central database stored in the cloud.
Because of this an expensive delivery system implemented across the country of Kuwait was enabled to continue without the losses incurred by identity theft and without the need for expensive replacement.